![SOLVED: 8 (a) Define the field F = GF(8) = Zz[x]lk' +x+1) What does x` equal in F ? What is the characteristic of F ? (b) Write out the 8 elements SOLVED: 8 (a) Define the field F = GF(8) = Zz[x]lk' +x+1) What does x` equal in F ? What is the characteristic of F ? (b) Write out the 8 elements](https://cdn.numerade.com/ask_images/6d8ef00943b4482db121d25f000a095b.jpg)
SOLVED: 8 (a) Define the field F = GF(8) = Zz[x]lk' +x+1) What does x` equal in F ? What is the characteristic of F ? (b) Write out the 8 elements
![PDF] On the enumeration of irreducible polynomials over GF(q) with prescribed coefficients | Semantic Scholar PDF] On the enumeration of irreducible polynomials over GF(q) with prescribed coefficients | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/56d6fadf3c2f956356ea875978169f3118166a43/29-Table1-1.png)
PDF] On the enumeration of irreducible polynomials over GF(q) with prescribed coefficients | Semantic Scholar

Table 2. Frequency of GF products being purchased based on broad product categories in 2016 and 2019 (2015: n=120, 2019: n=493) : Gluten-free Products in the UK Retail Environment. Availability, Pricing, Consumer

The Computerized Generation of Fractional‐replicate Designs Using Galois Fields and Hadamard Matrices - Zemroch - 2015 - Quality and Reliability Engineering International - Wiley Online Library






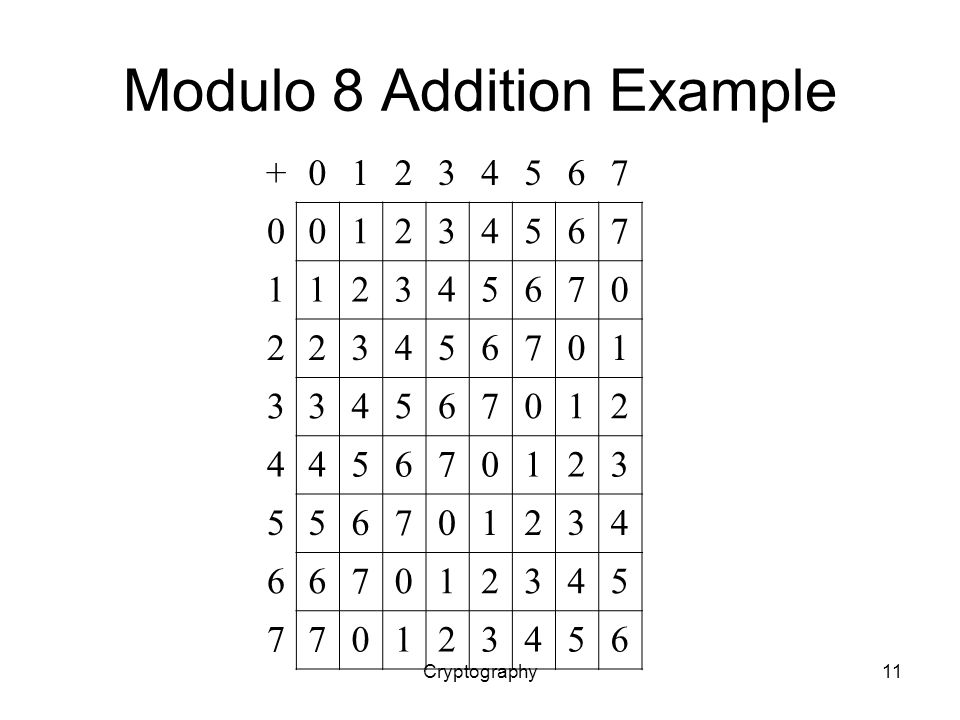





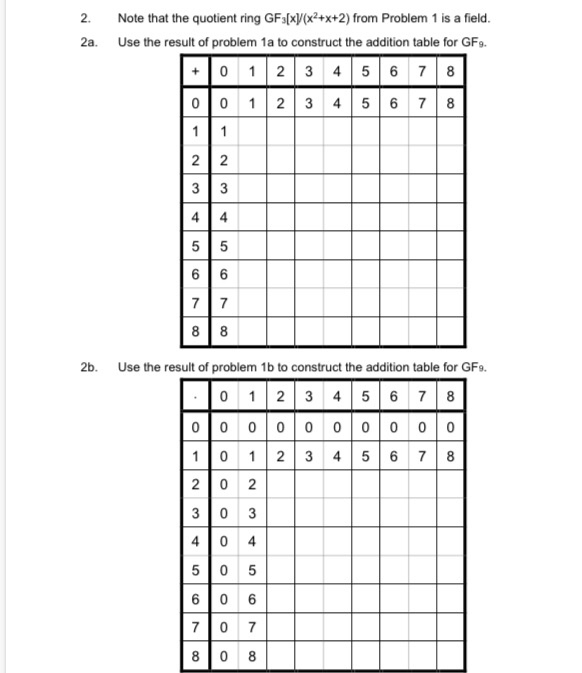
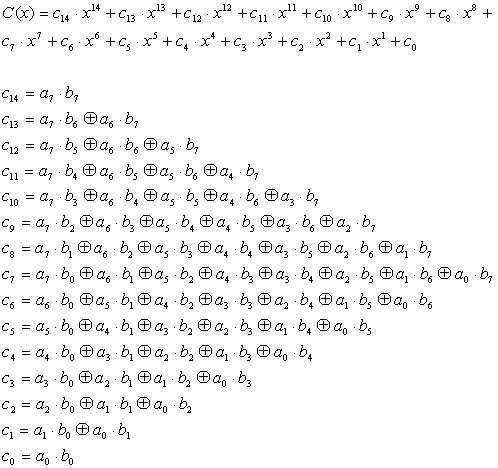



![Solved Produce a table for GF(8) = Z2[y]/(y^3 + y + 1) in | Chegg.com Solved Produce a table for GF(8) = Z2[y]/(y^3 + y + 1) in | Chegg.com](https://d2vlcm61l7u1fs.cloudfront.net/media%2F02d%2F02d8fe1e-3e86-427b-9c00-a93f7b0b9ee2%2FphpqM3enr.png)

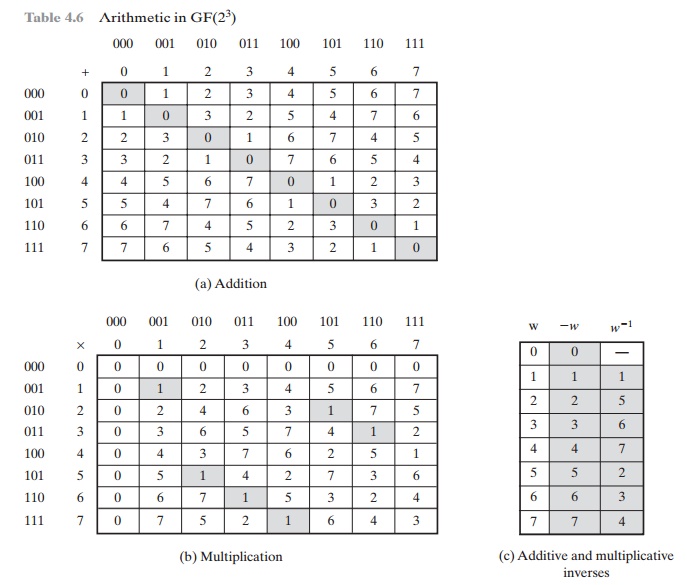
.jpg)